If you’re a credit insurer, the GLBA Safeguards Rule directly applies to you. This federal regulation requires financial institutions, including credit insurers, to implement strict measures to protect customer data. Non-compliance can lead to hefty fines, legal consequences, and reputational harm.
Here’s what you need to know:
- Key Requirement: Develop a written information security program to protect customer data.
- Core Steps:
- Appoint a "Qualified Individual" to oversee the program.
- Conduct regular, documented risk assessments.
- Implement safeguards: administrative, technical (like encryption and MFA), and physical.
- Vendor Oversight: Ensure third-party providers meet security standards through contracts and monitoring.
- Breach Reporting: Notify the FTC within 30 days if a breach affects 500+ consumers.
These steps ensure compliance and protect sensitive customer information. Below, we’ll break down the details and how to meet these requirements efficiently.
GLBA Safeguards Rule Compliance Requirements for Credit Insurers
Compliance with the FTC‘s GLBA Safeguards Rule
Core Requirements of the Safeguards Rule for Credit Insurers
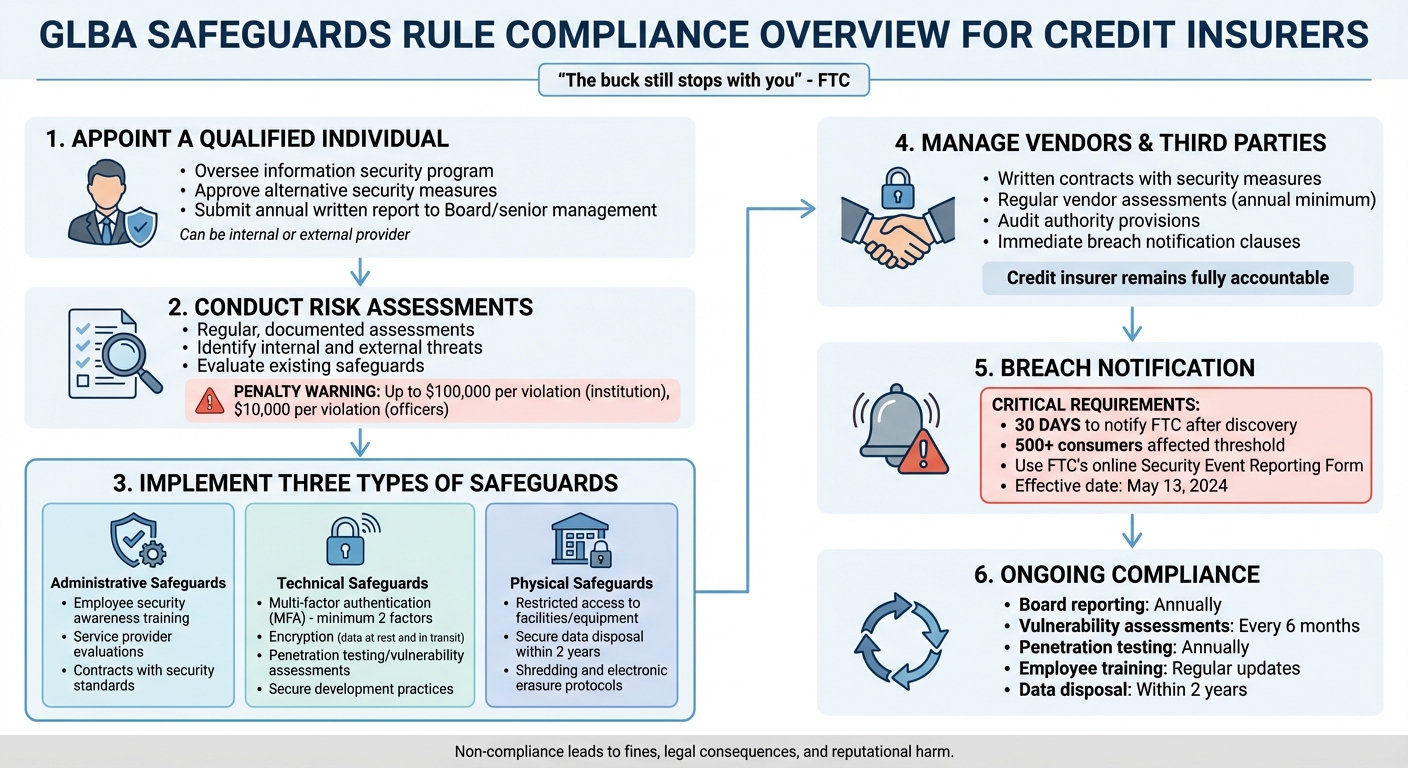
The GLBA Safeguards Rule outlines compliance into three main areas – administrative, technical, and physical safeguards. These categories define the steps credit insurers must take to secure customer information.
Appointing a Qualified Individual
Credit insurers are required to appoint a "Qualified Individual" to manage their information security program. While a specific degree isn’t mandatory, this person should have relevant experience tailored to the organization’s needs.
This individual can be an internal team member or an external provider under the insurer’s supervision. Their responsibilities include approving alternative security measures when standard practices, like encryption, aren’t practical. They must also submit an annual written report to the Board of Directors or senior management, detailing compliance, risk management efforts, and security incidents.
Conducting Written Risk Assessments
Credit insurers must carry out regular, documented risk assessments to identify potential threats – both internal and external – that could jeopardize customer information. These assessments should include clear criteria for evaluating risks and determining whether existing safeguards are adequate.
While institutions managing data for fewer than 5,000 consumers may not be required to conduct written risk assessments, doing so is still a smart practice. For larger organizations, thorough documentation is critical, as non-compliance could lead to fines of up to $100,000 per violation. Individual officers may also face penalties of up to $10,000 per violation.
"A risk assessment is only as good as the evidence it collects. Because asking teams if they have certain controls in place is one thing. Getting actual proof those controls exist is another." – SaltyCloud Research Team
Once risks are identified, insurers must act by implementing targeted administrative, technical, and physical safeguards.
Implementing Administrative, Technical, and Physical Safeguards
After identifying risks, insurers need to establish safeguards across all three categories to mitigate vulnerabilities.
- Administrative Safeguards: Employee security awareness training is essential, with specialized sessions for those handling security responsibilities. Regular evaluations of service providers are required, and contracts must include clear security standards.
- Technical Safeguards: Robust measures are necessary to protect systems. Multi-factor authentication (MFA) is mandatory, requiring at least two verification factors – such as a password, a security token, or biometrics. Customer data must be encrypted both during transmission and while stored. If encryption isn’t feasible, alternative controls must be formally approved by the Qualified Individual. Additional steps include regular penetration testing, vulnerability assessments, or continuous monitoring, as well as secure development practices for both in-house and third-party applications.
- Physical Safeguards: Access to buildings, offices, and equipment housing customer information should be restricted to authorized personnel. Customer data must be securely disposed of within two years unless retention is legally or operationally required. This includes shredding paper records and securely erasing electronic media.
Below is a summary of the key requirements for each safeguard category:
| Safeguard Category | Key Requirement | Implementation Detail |
|---|---|---|
| Administrative | Risk Assessment | Conduct and document assessments with clear evaluation criteria. |
| Technical | MFA | Require at least two factors (e.g., password, biometrics) for system access. |
| Technical | Encryption | Encrypt customer data at rest and in transit; if not feasible, formally approve alternatives. |
| Physical | Data Disposal | Securely dispose of customer data within two years unless legally required to retain it. |
| Administrative | Board Report | Submit an annual report covering compliance, risk management, and security incidents. |
Vendor and Third-Party Management Requirements
Credit insurers rely heavily on external vendors for essential operations like cloud storage, payment processing, and customer management. According to the GLBA Safeguards Rule, any vendor that receives, processes, or accesses customer information is classified as a service provider. However, the credit insurer remains fully accountable for safeguarding that data. The Federal Trade Commission (FTC) emphasizes this responsibility, stating, "If your company brings in a service provider to implement and supervise your program, the buck still stops with you. It’s your company’s responsibility to designate a senior employee to supervise that person." This dynamic underscores the need for a thorough evaluation of each vendor’s security practices.
Evaluating Vendor Security Practices
Before entering into any agreement, it’s crucial to assess a vendor’s ability to protect sensitive customer data. This evaluation should examine their technical expertise, track record in security, and understanding of the data’s importance.
Start by identifying the specific customer information the vendor will handle. For example, a vendor managing policyholder payments demands closer scrutiny than one supplying office equipment. Vendors should provide detailed, verifiable security documentation, such as SOC 2 reports, penetration test results, or certifications like ISO 27001. Once their security capabilities are confirmed, these expectations need to be clearly outlined in a written agreement.
Contractual Requirements and Monitoring
Once a vendor is selected, the Safeguards Rule mandates a written contract specifying the security measures they must implement and maintain. These contracts should detail required security protocols, monitoring procedures, and plans for regular reassessments.
Ensure the contract includes provisions requiring vendors to protect customer information and grants your organization the authority to audit their compliance. It should also require vendors to notify you immediately in the event of a security breach, enabling swift action. This aligns with the FTC’s 30-day breach notification guideline. Additionally, the contract should account for updates in technology and business processes to address emerging security threats.
Vendor oversight doesn’t stop with a signed contract. Schedule annual reviews for all vendors, with more frequent assessments for those considered high-risk. Your Qualified Individual should also include an evaluation of these vendor arrangements in their annual report to the Board of Directors, ensuring ongoing accountability and compliance.
sbb-itb-b840488
Incident Response and Breach Notification
No system is completely immune to breaches. That’s why, beyond conducting risk assessments and implementing safeguards, having a proactive plan to handle incidents is critical. The GLBA Safeguards Rule requires credit insurers to be prepared for potential breaches with a detailed incident response plan and clear procedures for breach notifications.
Developing an Incident Response Plan
Under the Safeguards Rule, having a written incident response plan (IRP) is not optional. This plan must address any "security event", which includes unauthorized access to or misuse of customer information. Your IRP should cover the following key components:
- Objectives: Define the purpose and goals of the plan.
- Technical and administrative procedures: Outline the steps for identifying, containing, and resolving incidents.
- Roles and decision authority: Specify who is responsible for what during an incident.
- Communication protocols: Establish how and when to notify key stakeholders.
- Remediation steps: Detail how to mitigate damage and prevent future incidents.
- Documentation and reporting: Keep thorough records of the incident and actions taken.
- Post-incident review: Assess what happened and improve future response strategies.
Communication is a particularly important part of the IRP. Your plan should include clear protocols for notifying management, the Board of Directors, regulators, law enforcement, and affected customers. If a vendor experiences a breach, they must notify you immediately so you can meet the FTC’s reporting requirements. This integration ensures your response plan aligns with the broader GLBA compliance framework.
Breach Notification Requirements
Once an IRP is in place, the next step is ensuring clear and timely breach notifications. As of May 13, 2024, the Safeguards Rule amendment enforces strict notification requirements. For credit insurers, reporting breaches promptly is mandatory. If a "notification event" occurs – defined as unauthorized access to unencrypted data involving at least 500 consumers – you must notify the FTC within 30 days of discovering the breach.
The FTC takes a broad view of "customer information", including any nonpublic personal details, not just highly sensitive data. The moment a breach is detected, the 30-day notification clock begins. The FTC presumes that unauthorized access to unencrypted data equates to unauthorized acquisition unless you can provide strong evidence to the contrary. Additionally, encrypted data is treated as unencrypted if the encryption key was also compromised.
As Lesley Fair, Senior Attorney at the FTC, explains:
"Unauthorized acquisition will be presumed to include unauthorized access to unencrypted customer information unless you have reliable evidence showing that there has not been, or could not reasonably have been, unauthorized acquisition of such information".
Here are the key reporting requirements:
| Requirement | Detail |
|---|---|
| Reporting Deadline | Within 30 days of discovery |
| Reporting Threshold | 500 or more consumers affected |
| Reporting Method | FTC’s online Security Event Reporting Form |
| Required Information | Institution name/contact, types of information involved, date/date range, event description, number of consumers affected |
Use the FTC’s online reporting form to provide the necessary details. If you don’t have the exact number of affected consumers at the 30-day mark, submit the best information available and update the report later as needed. Keep in mind, the FTC plans to publish breach notices on its website, which could increase the likelihood of class-action lawsuits. If law enforcement requests a delay in notification, you can mark the "Law Enforcement Delay Requested" box.
To respond efficiently, maintain an up-to-date data map showing where all customer information is stored. This will help you quickly assess whether the 500-consumer threshold has been reached. Remember, the 30-day clock starts as soon as any employee, officer, or agent becomes aware of the incident – not when senior management is informed.
Maintaining Compliance Over Time
Once your core safeguards and vendor controls are in place, the next step is ensuring they stay effective over time. Compliance isn’t a one-and-done task – it’s a continuous effort to keep up with evolving risks. As the Federal Trade Commission (FTC) aptly states:
"The only constant in information security is change – changes to your operations, changes based on what you learn during risk assessments, changes due to emerging threats, changes in personnel, and changes necessitated by other circumstances…"
To keep your security program effective, it must adapt to new threats, include regular employee training, and undergo systematic monitoring.
Training Employees on Data Security
A strong training program is key to maintaining compliance. Start with general awareness training for all employees, then provide specialized instruction for security staff on technical safeguards and threat detection. These programs should reflect the latest insights from regular risk assessments and emerging threats. It’s also important to document completed training sessions. The FTC underscores the importance of well-trained staff:
"a financial institution’s information security program is only as effective as its least vigilant staff member"
.
Continuous Monitoring and Review
To stay ahead of potential threats, you’ll need to implement either continuous system monitoring or a structured testing schedule. For example, annual penetration testing paired with vulnerability assessments every six months can help identify weaknesses before they’re exploited. While continuous monitoring provides real-time insights into unauthorized access and potential attacks, periodic testing offers a chance to reassess and strengthen your defenses.
Additionally, your designated Qualified Individual should prepare a written report at least once a year for the Board of Directors or senior management. This report should cover the overall status of your security program, recent risk assessments, and any security events . Reassessments should also be conducted whenever significant changes occur, such as new servers, platforms, business processes, mergers, or vendor arrangements. Regular reviews of access controls are equally important to ensure employees only have access to the customer information necessary for their roles. Service providers should also be reviewed periodically to confirm they meet the required safeguards.
By integrating vendor oversight, risk assessments, and continuous monitoring, you can ensure your safeguards remain effective against new and emerging threats.
| Activity | Interval |
|---|---|
| Board/Senior Management Reporting | At least annually |
| Vulnerability Assessments (if not using continuous monitoring) | Every six months |
| Penetration Testing (if not using continuous monitoring) | Annually |
| Risk Reassessments | Periodically and after material changes |
| Employee Training Updates | Regular refreshers based on new risks |
| Data Disposal | Within two years of last use |
These practices not only reinforce your initial safeguards but also ensure your security measures evolve alongside changes in your operations and the broader threat landscape.
Conclusion
The GLBA Safeguards Rule isn’t just a guideline for credit insurers – it’s a legal obligation designed to ensure that customer data is well-protected. Samuel Levine, Director of the FTC’s Bureau of Consumer Protection, puts it plainly:
"Financial institutions and other entities that collect sensitive consumer data have a responsibility to protect it."
To comply, organizations must follow specific steps, including appointing a Qualified Individual, conducting and documenting risk assessments, implementing multi-factor authentication and encryption, managing vendor relationships, maintaining a detailed incident response plan, and reporting breaches that impact 500 or more consumers within 30 days.
The updated rule also emphasizes the importance of technical measures like ongoing system testing, comprehensive employee training, and annual reporting to ensure robust security practices.
Protecting customer data isn’t just about meeting regulatory requirements – it’s essential for maintaining customer trust and safeguarding a company’s reputation. With the FTC actively enforcing these standards, non-compliance can lead to hefty penalties, loss of consumer confidence, and long-term reputational harm. Prioritizing these measures is critical for sustained success and compliance.
FAQs
What skills and authority should the ‘Qualified Individual’ have to manage the information security program under the GLBA Safeguards Rule?
Under the GLBA Safeguards Rule, credit insurers are required to designate a Qualified Individual to oversee their information security program. This person should possess a deep understanding of the organization’s operations, existing security protocols, and any risks that could compromise customer information. They also need the authority to allocate resources, guide staff, and enforce security policies effectively.
Essentially, the Qualified Individual serves as the program’s coordinator, handling tasks like conducting risk assessments, managing relationships with service providers, and delivering regular updates on security issues to senior leadership or the board. Their role is crucial in maintaining compliance and safeguarding sensitive customer data.
How can credit insurers ensure their vendors comply with the GLBA Safeguards Rule?
Credit insurers can help ensure their vendors comply with the GLBA Safeguards Rule by setting up a clear and organized oversight process. Start by performing a thorough risk assessment to evaluate how each vendor accesses and handles sensitive customer data. These findings should then be outlined in a written information security plan, as required by the rule.
To reinforce compliance, include specific contractual obligations in vendor agreements. These should cover key areas like encryption standards, access controls, and breach notification protocols. Beyond the contracts, it’s essential to keep a close eye on vendor compliance. This can be done through regular audits, security assessments, or other methods of gathering evidence. Any gaps or issues identified should be addressed immediately.
Additionally, vendors should be required to take part in ongoing security training and participate in incident response drills. Keeping detailed records of these efforts is just as important, as it demonstrates a commitment to compliance. By combining risk assessments, strong vendor contracts, regular monitoring, and continuous training, credit insurers can ensure their vendors uphold the necessary standards to protect customer information.
What are the key steps in creating an effective data breach response plan?
An effective data breach response plan lays out clear, actionable steps to manage incidents quickly and limit the damage. The first priority is to secure the affected systems to stop any further data loss. This means isolating compromised systems, applying necessary patches, and disabling any impacted accounts.
The next step is to assemble a response team. This team should include IT and security professionals, legal advisors, communications staff, and senior management. Their job is to investigate the breach, identify how it happened, and determine the extent of the damage. If needed, bring in forensic experts to preserve evidence and conduct a thorough analysis. Legal advisors play a key role here, ensuring compliance with the notification requirements of the GLBA Safeguards Rule and relevant state laws. They’ll also guide the process of notifying affected individuals, if required.
Finally, it’s essential to address vulnerabilities and document findings. Take corrective actions to fix security gaps, update internal policies, and provide employees with additional training to reduce the risk of future breaches. Prepare a detailed post-incident report to refine your response strategy and stay aligned with regulatory standards.